Enable Single Sign-On
Utilize Single Sign-On and enable Users to authenticate once and access mutliple applications and services deployed within an ecosystem or federation.
External applications and platforms can utilize Raidiam Connect as an OIDC-compliant Identity Provider (IDP). The integration is based on the Financial Grade API (FAPI) standard and uses:
-
Pushed Authorization Requests (PAR)
-
Authorization Code Flow
-
Proof Key of Code Exchange (PKCE)
Authorization Code Flow
In Authorization Code Flow -- defined in the OAuth 2.0 Authorization Framework (RFC6749) specification -- an authorization server sends a temporary (authorization) code to a client application. The code is exchanged for security tokens: access tokens, refresh tokens, and ID tokens. This flow is available for confidential clients, for example, web applications with a backend that can store credentials securely. This way, the client can obtain one or more of the following token types:
The authorization code proves to the authorization server that the client requesting a token is permitted to do so. The user consents that the client can access the resource before the authorization server passes the code.
Pushed Authorization Requests
OAuth Pushed Authorization
Requests (PAR RFC9126) is an
OAuth 2.0 extension for the PAR endpoint that allows client applications to push
the payloads of authorization requests to authorization server via direct
requests to the PAR endpoint. In return, the client application receives a
request URI that is used as a reference to the previously sent payload data in a
subsequent call to the authorization server's /authorization endpoint.
Proof Key of Code Exchange
The Proof Key of Code Exchange (PKCE) is an extension of the standard authorization code flow. It is designed to be a secure substitute for the implicit flow for single-page applications (SPA) or native applications.
Authorization code grant with PKCE introduces a technique to prevent unauthorized access to resources in the case of code interception. Due to the Raidiam Authorisation Server FAPI 2.0 Security Profile compliance, using PKCE is mandatory for all applications.
In PKCE, the client application generates a code_verifier and transforms it
into code_challenge. code_verifier is a random key that prevents the
authorization code from being intercepted. code_verifieris generated by the
client application for every authorization request and transformed into
code_challengeaccording to the code_challenge_method set for the client
application in advance. It’s mandatory to set the code_challenge_method value
to S256.
While sending the request to the PAR or authorization endpoints, the client application must include the code challenge in the request. While requesting token, the requests to the authorization server must also include the code challenge of the same value that was sent to the PAR or authorization endpoint.
Integration Pattern for SSO
To integrate with Raidiam for authentication, client applications need to push their authorization requests to Raidiam Authorisation Servers in order to obtain the request URI that refers to their subsequent call to the OAuth authorization endpoint.
Once the application request authorization, the user is redirected to Raidiam Login Screen where they can authenticate themselves. Once authenticated, the user provides their consent to share their data stored by Raidiam and gets redirected back to the application.
At the same time, the client application receives an authorization code that can be exchanged for tokens. The application can utilize the tokens issued by Raidiam's Authorization Server in order to access its APIs or get information about the authentication event and the user.
Setting Up Directory
-
Within your application, register the same
redirect_urithat you will use in the Single Sign-On process.The redirect URI tells Raidiam's Authorization Server where to redirect the user after they authenticate themselves and provide their consent.
You can register multiple redirect URIs.
warningAfter creating your software statement, any new
redirect_urirequires a manual update from Raidiam's side. -
Provide your Trust Framework Administrator with a client identifier of your application (Software Statement ID) -- enabling the administrator to configure the application to request necessary scopes.
Discover Raidiam Authorization Server Configuration
Add Raidiam Authorization Server's OIDC Discovery (/.well-known) endpoint to your application. Utilize any OAuth library you want.
For example, the URLs for Raidiam's Demo Environment look like the following:
-
OpenID Discovery:
https://auth.demo.raidiam.io/.well-known/openid-configuration -
Authorization endpoint:
https://auth.demo.raidiam.io/auth -
Token endpoint:
https://matls-auth.demo.raidiam.io/token -
User Info endpoint:
https://auth.demo.raidiam.io/me
Postman Collection
You can utilize the below Postman API collection to quickly test the integration:
{
"info": {
"_postman_id": "9a531af2-d63a-4bc6-bdc9-d92d3a8bdfe9",
"name": "SSO - Raidiam Connect Example",
"schema": "https://schema.getpostman.com/json/collection/v2.1.0/collection.json",
"_exporter_id": "19018955"
},
"item": [
{
"name": "SSORequest with TrustFramework Profile",
"protocolProfileBehavior": {
"disabledSystemHeaders": {
"accept": true
}
},
"request": {
"auth": {
"type": "noauth"
},
"method": "POST",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"url": {
"raw": "{{auth}}?scope=openid trust_framework_profile&client_id={{clientID}}&redirect_uri={{redirectURI}}&state={{state}}&nonce={{nonce}}&response_type=code id_token&code_challenge=hsCf5fSU7C4zy0EyarwqHPWN3ABmP6hH9pPyFjBUFo4&code_challenge_method=S256",
"host": [
"{{auth}}"
],
"query": [
{
"key": "scope",
"value": "openid trust_framework_profile"
},
{
"key": "client_id",
"value": "{{clientID}}"
},
{
"key": "redirect_uri",
"value": "{{redirectURI}}"
},
{
"key": "state",
"value": "{{state}}"
},
{
"key": "nonce",
"value": "{{nonce}}"
},
{
"key": "response_type",
"value": "code id_token"
},
{
"key": "code_challenge",
"value": "hsCf5fSU7C4zy0EyarwqHPWN3ABmP6hH9pPyFjBUFo4"
},
{
"key": "code_challenge_method",
"value": "S256"
}
]
}
},
"response": []
},
{
"name": "SSOrequest with OpenID Profile + TrustFrameworkProfile",
"protocolProfileBehavior": {
"disabledSystemHeaders": {
"accept": true
}
},
"request": {
"auth": {
"type": "noauth"
},
"method": "POST",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "urlencoded",
"urlencoded": [
{
"key": "grant_type",
"value": "client_credentials",
"type": "text"
},
{
"key": "scope",
"value": "directory:software",
"type": "text"
},
{
"key": "client_id",
"value": "d3b64db5-2a54-45a1-8dec-ab278f8e30db",
"type": "text"
}
]
},
"url": {
"raw": "{{auth}}?scope=openid profile trust_framework_profile&client_id={{clientID}}&redirect_uri={{redirectURI}}&nonce={{nonce}}&response_type=code id_token&code_challenge=ZJXBMj6ffuUYVfPD-GdHWGIhUbIH1plqnRrR7WYijkY&code_challenge_method=S256",
"host": [
"{{auth}}"
],
"query": [
{
"key": "scope",
"value": "openid profile trust_framework_profile"
},
{
"key": "client_id",
"value": "{{clientID}}"
},
{
"key": "redirect_uri",
"value": "{{redirectURI}}"
},
{
"key": "state",
"value": "{{state}}",
"disabled": true
},
{
"key": "nonce",
"value": "{{nonce}}"
},
{
"key": "response_type",
"value": "code id_token"
},
{
"key": "code_challenge",
"value": "ZJXBMj6ffuUYVfPD-GdHWGIhUbIH1plqnRrR7WYijkY"
},
{
"key": "code_challenge_method",
"value": "S256"
}
]
}
},
"response": []
},
{
"name": "Request token",
"request": {
"method": "POST",
"header": [
{
"key": "Content-Type",
"value": "application/x-www-form-urlencoded;charset=UTF-8",
"type": "text"
},
{
"key": "Content-Length",
"value": "196",
"type": "text",
"disabled": true
},
{
"key": "Accept",
"value": "application/json;charset=UTF-8",
"type": "text"
}
],
"body": {
"mode": "urlencoded",
"urlencoded": [
{
"key": "grant_type",
"value": "authorization_code",
"type": "text"
},
{
"key": "redirect_uri",
"value": "https://www.example.com/cb",
"type": "text"
},
{
"key": "code",
"value": "tQes2Qdv71SigLej-H5JftWoGzkmDrmcOv0-I0e8QIW",
"type": "text"
},
{
"key": "client_id",
"value": "4f5e14e7-2cb8-476c-8bcf-7f9899f5dcd8",
"type": "text"
}
]
},
"url": {
"raw": "https://matls-auth.sandbox.directory.openbankingbrasil.org.br/token",
"protocol": "https",
"host": [
"matls-auth",
"sandbox",
"directory",
"openbankingbrasil",
"org",
"br"
],
"path": [
"token"
]
}
},
"response": []
},
{
"name": "/Me Request",
"request": {
"method": "GET",
"header": []
},
"response": []
}
],
"variable": [
{
"key": "authURL",
"value": "https://auth.sandbox.directory.openbankingbrasil.org.br/auth?"
},
{
"key": "auth",
"value": "https://auth.sandbox.directory.openbankingbrasil.org.br/auth"
},
{
"key": "tokenURL",
"value": "https://matls-auth.sandbox.directory.openbankingbrasil.org.br/token"
},
{
"key": "clientID",
"value": "4f5e14e7-2cb8-476c-8bcf-7f9899f5dcd8"
},
{
"key": "nonce",
"value": "gXGldLyytu"
},
{
"key": "state",
"value": "xyzABC123"
},
{
"key": "redirectURI",
"value": "https://www.example.com/cb"
}
]
}
Push Authorization Request
Below, you can find a Postman implementation of a pushed authorization request (PAR).
{
"info": {
"_postman_id": "3ac5b905-75d5-49be-b460-e31e63706470",
"name": "SSO - Raidiam Connect Example PAR",
"schema": "https://schema.getpostman.com/json/collection/v2.1.0/collection.json",
"_exporter_id": "19018955"
},
"item": [
{
"name": "PAR - Working (TLS_Client_Auth)",
"request": {
"method": "POST",
"header": [],
"body": {
"mode": "urlencoded",
"urlencoded": [
{
"key": "response_type",
"value": "code",
"type": "text"
},
{
"key": "code_challenge_method",
"value": "S256",
"type": "text"
},
{
"key": "nonce",
"value": "gXGldLyaatu",
"type": "text"
},
{
"key": "client_id",
"value": "4f5e14e7-2cb8-476c-8bcf-7f9899f5dcd8",
"type": "text"
},
{
"key": "scope",
"value": "openid trust_framework_profile",
"type": "text"
},
{
"key": "redirect_uri",
"value": "https://www.example.com/cb",
"type": "text"
},
{
"key": "state",
"value": "xyaaaABC124",
"type": "text"
},
{
"key": "code_challenge",
"value": "47DEQpj8HBSa-_TImW-5JCeuQeRkm5NMpJWZG3hSuFU",
"type": "text"
}
]
},
"url": {
"raw": "https://matls-auth.sandbox.directory.openbankingbrasil.org.br/request",
"protocol": "https",
"host": [
"matls-auth",
"sandbox",
"directory",
"openbankingbrasil",
"org",
"br"
],
"path": [
"request"
],
"query": [
{
"key": "client_assertion",
"value": "eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiI0ZjVlMTRlNy0yY2I4LTQ3NmMtOGJjZi03Zjk4OTlmNWRjZDgiLCJpc3MiOiI0ZjVlMTRlNy0yY2I4LTQ3NmMtOGJjZi03Zjk4OTlmNWRjZDgiLCJhdWQiOiJodHRwczovL21hdGxzLWF1dGguc2FuZGJveC5kaXJlY3Rvcnkub3BlbmJhbmtpbmdicmFzaWwub3JnLmJyIiwiZXhwIjoxNjc1Mjk5MDgyLCJqdGkiOiIxMzc4M2QyZC1lODgxLTQyMGEtOGRhOS1jMjdhN2M4ZDA2MDgiLCJpYXQiOjE2NzUyOTUuNDgyfQ.fnoxgvCDTp7PbHINdngelZqYlHUTOANVMIxJm6zoyo1cxvvkgicFO6wfy5fZaem0OvecI7YuekdCkzBb8MCAUdaUzaurfOisEJddiSE-jJZVrQf2rK5ZIC76faKBDJ1zUurrcjlZaB6sBLs4u3XyjZ33iumJkK9GpWfdpwOvI4TUU0k-aT_K9FfFmIIm4Qa-tJvGzqkYSAJ4hv1OjocXsqOanqCaxgIFb-Ra88qyT7p03ltEDSI9rgC9fJLrPjFyuC_qpzSIx6rENNwP7sPTPAUhE1mSjWDq5uILh9Go56n3flNduJP7slUspMO064-BgW_gW_mgmg8ziGXUdZ6dVQ",
"disabled": true
},
{
"key": "client_assertion_type",
"value": "urn%3Aietf%3Aparams%3Aoauth%3Aclient-assertion-type%3Ajwt-bearer",
"disabled": true
}
]
}
},
"response": []
}
],
"variable": [
{
"key": "authURL",
"value": "https://auth.sandbox.directory.openbankingbrasil.org.br/auth?"
},
{
"key": "auth",
"value": "https://auth.sandbox.directory.openbankingbrasil.org.br/auth"
},
{
"key": "tokenURL",
"value": "https://matls-auth.sandbox.directory.openbankingbrasil.org.br/token"
},
{
"key": "clientID",
"value": "4f5e14e7-2cb8-476c-8bcf-7f9899f5dcd8"
},
{
"key": "nonce",
"value": "gXGldLyytu"
},
{
"key": "state",
"value": "xyzABC123"
},
{
"key": "redirectURI",
"value": "https://www.example.com/cb"
}
]
}
For PAR, call the pushed_authorization_request_endpoint endpoint from the well-known. In this example, it's /request.
| Field | Required | Description | Value |
|---|---|---|---|
| client_id | yes | Retrieved from the Software StatementOAuth 2.0 Client Identifier valid at the Authorization Server. | my-client-app |
| response_type | yes | OAuth 2.0 Response Type value that determines the authorization processing flow to be used, including what parameters are returned from the endpoints used. | code |
| redirect_uri | Redirection URI to which the response is sent. Defined when creating the software statement (application).This URI MUST exactly match one of the Redirection URI values for the Client pre-registered at the OpenID Provider, with the matching performed as described in Section 6.2.1 of RFC3986 (Simple String Comparison). When using this flow, the Redirection URI SHOULD use the https scheme; however, it MAY use the http scheme, provided that the Client Type is confidential, as defined in Section 2.1 of OAuth 2.0, and provided the OP allows the use of http Redirection URIs in this case. The Redirection URI MAY use an alternate scheme, such as one that is intended to identify a callback into a native application. | ||
| scope | yes | OpenID Connect requests MUST contain the openid scope value. If the openid scope value is not present, the behavior is entirely unspecified. Other scope values MAY be present. Scope values used that are not understood by an implementation SHOULD be ignored.See Sections 5.4 and 11 for additional scope values defined by this specification. | openid trust_framework_profileoropenid profile trust_framework_profile |
| nonce | String value used to associate a Client session with an ID Token, and to mitigate replay attacks.The value is passed through unmodified from the Authentication Request to the ID Token. Sufficient entropy MUST be present in the nonce values used to prevent attackers from guessing values. For implementation notes, see Section 15.5.2. | ||
| response_mode | yes | Determines how the result of the authorization request is formatted.In this case, the query.jwt response mode indicates that the authorization response parameters will be encoded as a JWT and sent via the query string of the redirect_uri.This mode is part of the JARM (Joint Authentication Request Markup) extension to OAuth and OpenID Connect. The use of JARM provides an additional layer of security, ensuring the integrity and authenticity of the returned parameters. | query.jwt |
| state | no | Opaque value used to maintain state between the request and the callback.Typically, Cross-Site Request Forgery (CSRF, XSRF) mitigation is done by cryptographically binding the value of this parameter with a browser cookie. | |
| code_challenge | yes | Utilized in PKCE.Code challenge is a base64 URL-encoded result of transforming the code verifier using the SHA256 algorithm. | BASE64URL-ENCODE(SHA256(ASCII(code_verifier))) |
| code_challenge_method | yes | The algorithm used to create the code challenge. | S256 |
Sample request:
POST https://matls-auth.demo.raidiam.io/request
Body (x-www-form-urlencoded):
response_type=code
code_challenge_method=S256
nonce=gXGldLyaatu
client_id=b7add03c-b18e-495f-b6e5-499ef745a6b9
scope=openid trust_framework_profile
redirect_uri=https://www.example.com
state=xyaaaABC124
code_challenge=47DEQpj8HBSa-_TImW-5JCeuQeRkm5NMpJWZG3hSuFU
Sample response:
{"expires_in":60,"request_uri":"urn:ietf:params:oauth:request_uri:o34QcmivOOqJ_iuWqPmN6"}
Authorize Application
Using the Connect's /auth endpoint, build out the full request endpoint by
including the request URI you received in the previous section as a query
parameter.
Sample: https://auth.demo.raidiam.io/auth?request_uri=urn:ietf:params:oauth:request_uri:o34QcmivOOqJ_iuWqPmN6&client_id=b7add03c-b18e-495f-b6e5-499ef745a6b9
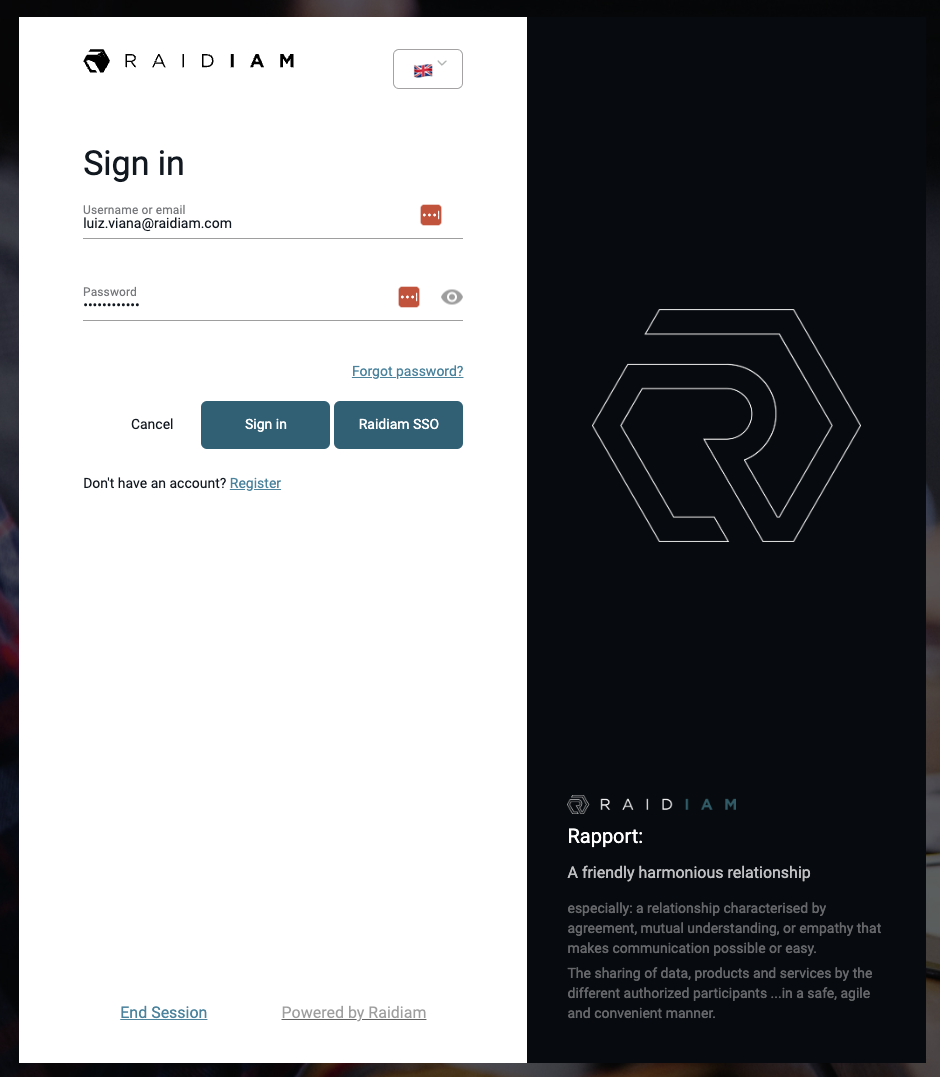
Authorization Server Authenticates End-User
Authorization Server Obtains End-User Consent/Authorization
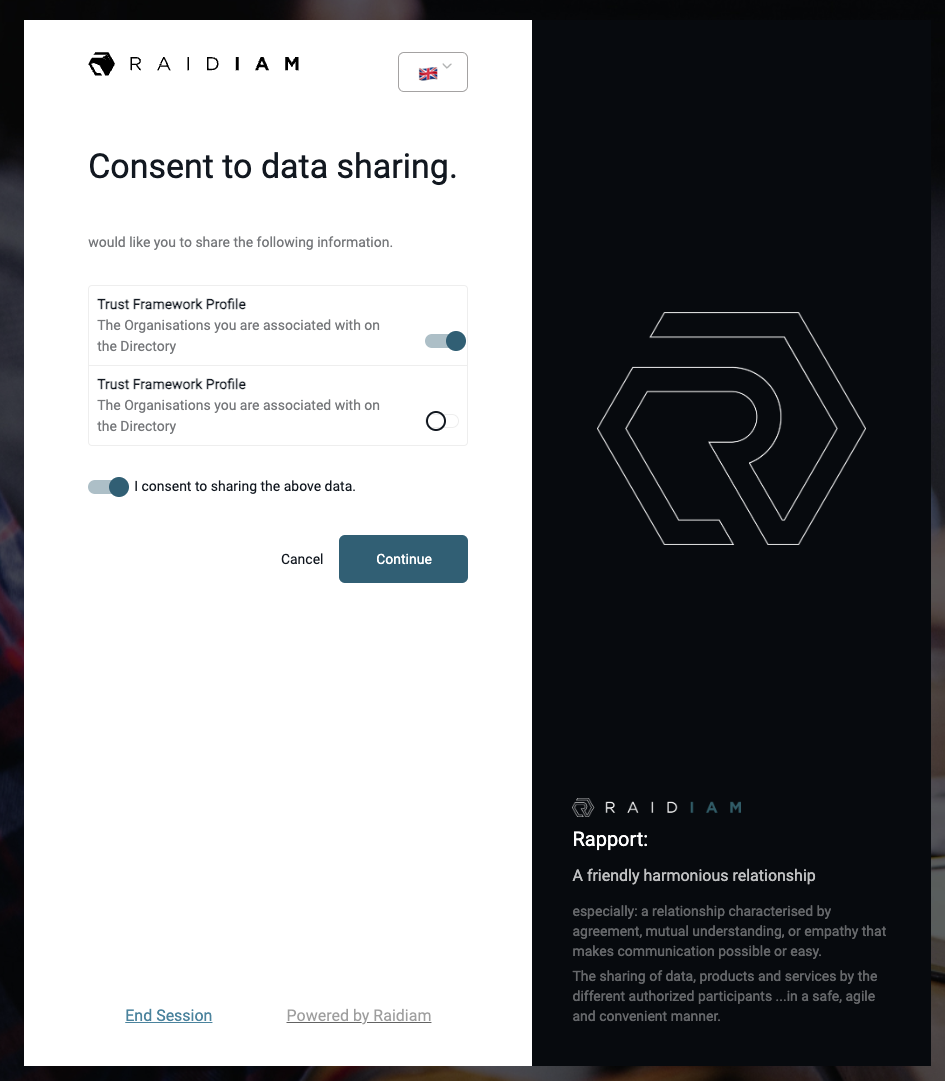
Authorization Server Redirects End-User Back to Client
The redirect URL now contains a JSON Web Token (JWT) with the authorization code.
Sample redirect:
https://www.example.com/?response=eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjE2MzIxNTEyMzM0MzctZjdiMzNlYWZmYyJ9.eyJjb2RlIjoiWEYzRXNKVElrcFRoSC12cXdvd0VFWG1Td1JFNDlnbmhvNkVMUURGWEZ1eSIsImF1ZCI6ImI3YWRkMDNjLWIxOGUtNDk1Zi1iNmU1LTQ5OWVmNzQ1YTZiOSIsImV4cCI6MTY5NDUyMjUxNSwiaXNzIjoiaHR0cHM6Ly9hdXRoLmRlbW8ucmFpZGlhbS5pbyJ9.OnxDxFmBiyLHXk5L91HTCreE6EY2BULH5kFEkAlgopJL4qynlKY2F3E075lnh4JGgG5bbzgHXwsSI1oTtBcoeoBrzzF1Z9Rd1qNV3KsFGjeyB1KeAhpoVxO34T5hPNnaYXYVxhoTDSsrsjnAdMvXluk6LF5HNT_GJfzE15O9PcHYlTsLTwRYTDt4G25HUzXLZWbYt58Kpjck0IYbs8_PTNi7Gzn-rC_dGn1uvW2wrIEPT-WqyznV9Ax5Svb2QwgGeq3ZtZEgpsnqA664MetJlq0PA30tw9FPABRtDx4l7KOAKU0VTjYgPMpY06TYCDhJC1GSBEo1CEcM0ZFIdSG6Pw
Remember to properly validate all the fields in the JWT as well as its signature
Within the JWT you can find the authorisation code: XF3EsJTIkpThH-vqwowEEXmSwRE49gnho6ELQDFXFuy
Get Tokens
With the code returned from the auth endpoint, call the token endpoint to get the user's information. You will need a transport certificate.
In order for the client to be able to talk to the directory and call the MTLS protected endpoints such as the token endpoint, it needs valid transport certificates. There is a good explanation on how to generate these on the 'Directory Operation Manual'
Token URL: https://matls-auth.demo.raidiam.io/token
Request Body:
grant_type:authorization_code
redirect_uri:https://www.example.com
code:XF3EsJTIkpThH-vqwowEEXmSwRE49gnho6ELQDFXFuy
client_id:b7add03c-b18e-495f-b6e5-499ef745a6b9
code_verifier:dBjftJeZ4CVP-mB92K27uhbUJU1p1r_wW1gFWFOEjXk
Since you’re using PKCE, you have to use the code_verifier information of the code_challenge provided.
Doing a POST with this information gives you:
{
"access_token": "Nqa7-dzlUFj4ZpL7k1a1VRRkOS8xzQyK29oozJiHUB5",
"expires_in": 3600,
"id_token": "eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjE2MzIxNTEyMzM0MzctZjdiMzNlYWZmYyJ9.eyJzdWIiOiJsdWl6LnZpYW5hQHJhaWRpYW0uY29tIiwidHhuIjoicTBSd01fdnprdjM5em9hMG5USkREYUptX1ZIcEhMelNoZUI3d2FLQi10VCIsInRydXN0X2ZyYW1ld29ya19wcm9maWxlIjp7ImJhc2ljX2luZm9ybWF0aW9uIjp7InN0YXR1cyI6IkFjdGl2ZSIsInVzZXJfZW1haWwiOiJsdWl6LnZpYW5hQHJhaWRpYW0uY29tIn0sImNlcnRpZmljYXRpb25fbWFuYWdlciI6ZmFsc2UsIm9yZ19hY2Nlc3NfZGV0YWlscyI6eyIwMmI2NDYzNF9jNzNlXzRlNTVfOWJiZl9iNGZkNGIxOTU2MmQiOnsib3JnX2FkbWluIjp0cnVlLCJvcmdfcmVnaXN0cmF0aW9uX251bWJlciI6Ikx1aXpUZXN0T3JnIiwib3JnYW5pc2F0aW9uX25hbWUiOiJMdWl6VGVzdE9yZyJ9fSwic3VwZXJfdXNlciI6dHJ1ZSwic3lzdGVtX3VzZXIiOnRydWV9LCJub25jZSI6ImdYR2xkTHlhYXR5IiwiYXRfaGFzaCI6ImtuQThhWjFqTDktSHlNUmZkYm1obXciLCJhdWQiOiJiN2FkZDAzYy1iMThlLTQ5NWYtYjZlNS00OTllZjc0NWE2YjkiLCJleHAiOjE2OTQ1MjYwODQsImlhdCI6MTY5NDUyMjQ4NCwiaXNzIjoiaHR0cHM6Ly9hdXRoLmRlbW8ucmFpZGlhbS5pbyJ9.eNsLp5rmZPKdo_T5SjFQko5nwrUBvycvmP1mHDjuzNr2lb_ykgk08N0XBBq1IXyMRaTrpuKi7q5zLyz6rxVPqA7rj-_JX_DG-PWf8nhiJ-q14TlSR8sLhXZo1EMvzSvUnawPs48pAoMiVb6ckcfRuNa-Wb9ib7UTtvbEXKaMwJHcWnjvsv3mkrcUPLJ0jnUT1y8pqB6nt4rluBTnd0ji_VHAHBnZat8D5QHjwrRK1CYarqBxc_s0KSZB-b-mZsdg51dHR89YyfHLWep_-xnlGlxJOFtUA_VroTIpy6fTT76QMXFV2dMHB78wkS0zFmCS0zfUXmcMsKTo-erG0mHsMw",
"scope": "openid trust_framework_profile",
"token_type": "Bearer"
}
Inspecting the ID token received gives you the JSON with information similar to the below:
{
"sub": "luiz.viana@raidiam.com",
"txn": "q0RwM_vzkv39zoa0nTJDDaJm_VHpHLzSheB7waKB-tT",
"trust_framework_profile": {
"basic_information": {
"status": "Active",
"user_email": "luiz.viana@raidiam.com"
},
"certification_manager": false,
"org_access_details": {
"02b64634_c73e_4e55_9bbf_b4fd4b19562d": {
"org_admin": true,
"org_registration_number": "LuizTestOrg",
"organisation_name": "LuizTestOrg"
}
},
"super_user": true,
"system_user": true
},
"nonce": "gXGldLyaaty",
"at_hash": "knA8aZ1jL9-HyMRfdbmhmw",
"aud": "b7add03c-b18e-495f-b6e5-499ef745a6b9",
"exp": 1694526084,
"iat": 1694522484,
"iss": "https://auth.demo.raidiam.io"
}
Alternatively, you can also use the access token to call the Connect's /me endpoint whenever needed.
Sample request:
GET https://matls-auth.demo.raidiam.io/me
Header: {Authorization: "Bearer Nqa7-dzlUFj4ZpL7k1a1VRRkOS8xzQyK29oozJiHUB5"}
Sample response:
{
"sub": "luiz.viana@raidiam.com",
"txn": "q0RwM_vzkv39zoa0nTJDDaJm_VHpHLzSheB7waKB-tT",
"trust_framework_profile": {
"basic_information": {
"status": "Active",
"user_email": "luiz.viana@raidiam.com"
},
"certification_manager": false,
"org_access_details": {
"02b64634_c73e_4e55_9bbf_b4fd4b19562d": {
"org_admin": true,
"org_registration_number": "LuizTestOrg",
"organisation_name": "LuizTestOrg"
}
},
"super_user": true,
"system_user": true
}
}
Get More Information About Authenticated User
If you require additional information such as the user's name and national ID
number (CPF for Brazil), you can add profile to your scope request.
By sending the scope openid profile trust_framework_profile, this is what
the ID token would contain:
{
"sub": "luiz.viana@raidiam.com",
"txn": "q0RwM_vzkv39zoa0nTJDDaJm_VHpHLzSheB7waKB-tT",
"trust_framework_profile": {
"basic_information": {
"status": "Active",
"user_email": "luiz.viana@raidiam.com"
},
"certification_manager": false,
"org_access_details": {
"02b64634_c73e_4e55_9bbf_b4fd4b19562d": {
"org_admin": true,
"org_registration_number": "LuizTestOrg",
"organisation_name": "LuizTestOrg"
}
},
"super_user": true,
"system_user": true
},
"email": "luiz.viana@raidiam.com",
"email_verified": true,
"phone_number": "+5584994170198",
"phone_number_verified": true,
"family_name": "Viana",
"given_name": "Luiz",
"name": "Luiz Viana"
}