Access Scopes
An access token scope is a parameter used in OAuth to define the specific
permissions or actions that the access token allows when accessing a resource on
behalf of a user. Scopes help control the level of access granted to the
application, ensuring that the token only has the permissions necessary for the
requested operation.
Using Access Scopes
An application can request one or more scopes. This information:
-
Must be included in the call to the PAR endpoint, OAuth Authorization Endpoint, and OAuth Token Endpoint.
-
Is presented to the user in the consent screen (after the call to the OAuth Authorization Endpoint)
The access token issued to the application is limited to the scopes granted by the user -- for OAuth Authorization Code Flow -- and to scopes requested by the applications in machine-to-machine scenarios using the OAuth Client Credentials Flow.
In Raidiam, the scopes your application can request are determined by the application's Role and its associated Metadata.
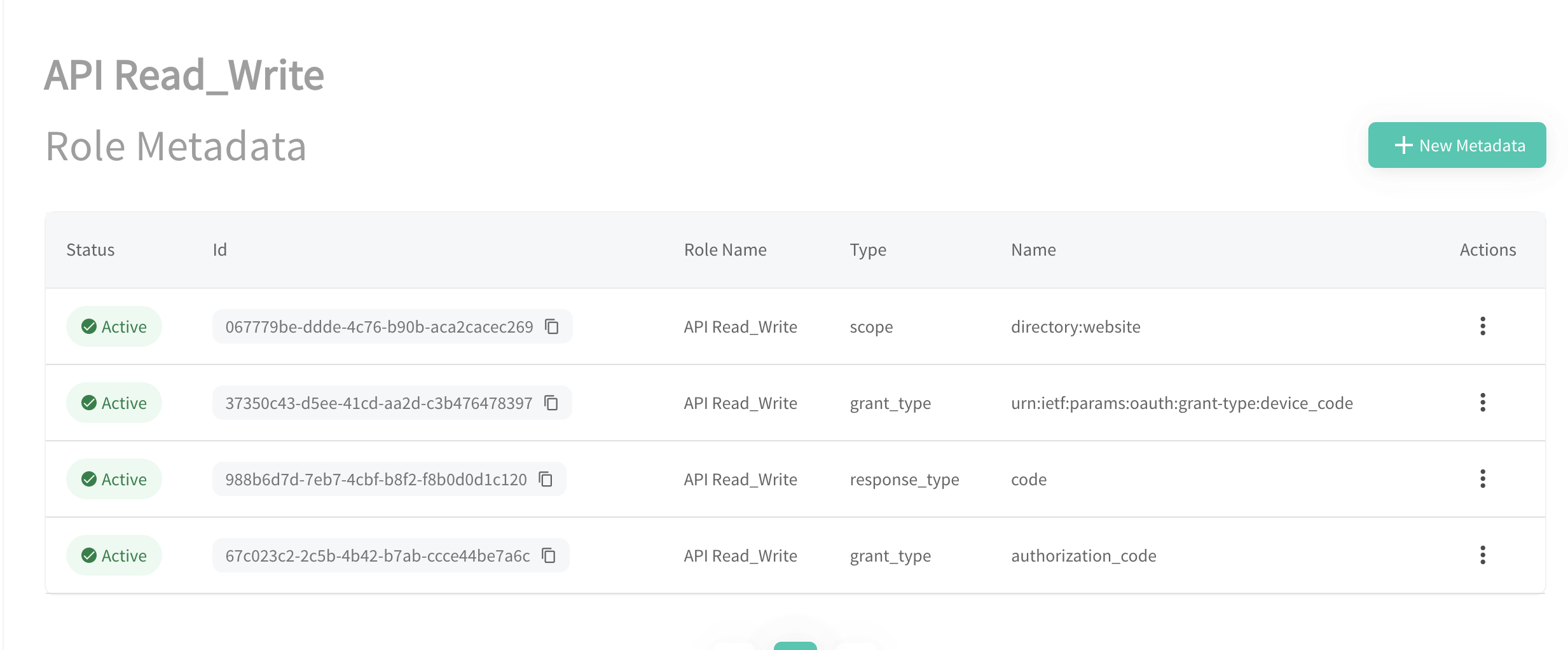
To request the directory:websitescope, the application needs to have the scope Role Metadata Type assigned with the value set to directory:website.
In Raidiam, all applications are assigned the client_credentials flow and directory:software scope by default.
Note that the application Role is not the value of the scope parameter.
Available Raidiam Access Scopes
Applications can use the following scopes to access Raidiam APIs:
directory:software
Used for client-management-related operations like getting a list of all applications registered within the ecosystem or federation, generating Software Statement Assertions, scanning for new Data Receiver applications, retrieval of public certificates, and more.
Additionally, with the directory:software scope, you can perform READ
operations on all resources available within the Trust Framework.
Application that has a token with the directory:software scope can perform
WRITE operations only on the APIs related to this application. In other
words, an application with this scope can request, for example, an
application-level certificate only for itself and not for other application.
Requesting the directory:software scope can be done using the client
credentials flow without involving the users.
directory:website
Used by applications to perform web-based operations like administering the underlying Trust Framework, onboarding Organisations, and more on behalf of a Super User, Data Administrator -- a Trust Framework Administrator -- or other User Type with appropriate permissions.
Requesting the directory:website scope implies using the OAuth Authorization
Code Flow and involves authenticating users and getting their consent.
If your organisation needs to get tokens with the directory:website scope in a
machine-to-machine scenario (with the Client Credentials Flow), it can be done
by creating a Role that has such metadata configured and assigning it to the
Organisation and Application. Contact your Trust Framework Administrator to
request such a role.
trust_framework_profile
Scope necessary when using the OAuth Authorization Code Flow and Raidiam Connect as a Single Sign On (SSO) provider to other external platforms.
OpenID Connect Access Scopes
The following OpenID Connect scopes are available to applications using the OAuth Authorization Code Flow:
openid
Used to indicate that the application intends to use OIDC to verify the user's identity.
profile
Used to get basic profile information like the user's name, family name, and more.
email
Used to get the user's email address.