Client Authentication with mTLS Certificate: self_signed_tls_client_auth vs tls_client_auth
TLS client authentication is a critical component in securing APIs and
services through mutual TLS (mTLS). Two widely used methods for mTLS client
authentication—self_signed_tls_client_auth and tls_client_auth—achieve
similar goals with very different trust models.
In this post, we’ll break down the differences between self-signed TLS client authentication and CA-signed TLS client authentication, compare their use cases, and walk through the authentication flows developers and security architects must implement. Whether you're designing internal microservices or building production-grade OAuth 2.0 integrations, this comparison will help you choose the right approach.
What Is TLS Client Authentication?
TLS client authentication enables a server to verify the identity of a client during the TLS handshake using X.509 certificates. It forms the foundation of mutual TLS (mTLS), where both the server and client present certificates and prove possession of private keys.
There are two common types of client authentication in mTLS:
-
tls_client_auth– uses certificates issued by a trusted Certificate Authority (CA) -
self_signed_tls_client_auth– uses self-signed certificates trusted manually by the server
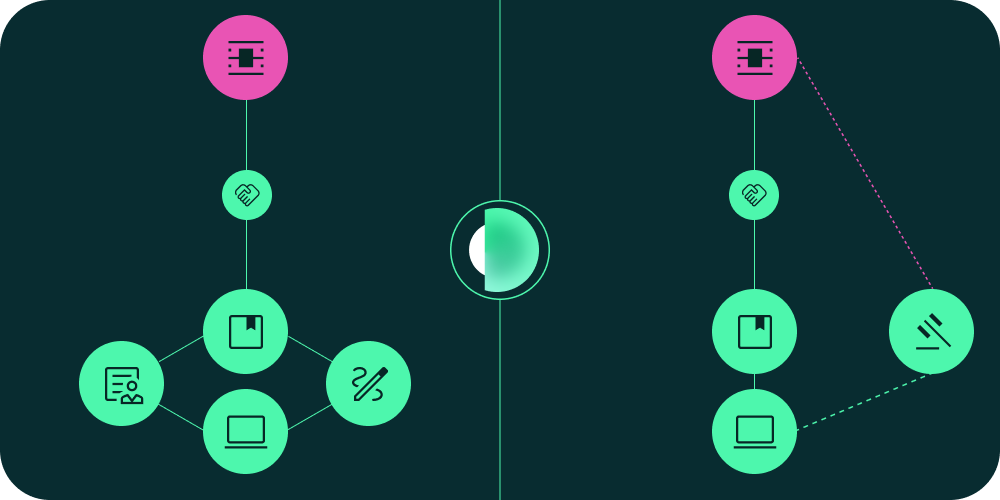
tls_client_auth: CA-Signed Certificate-Based Authentication
The tls_client_auth method is the standard approach for mTLS in production-grade
systems. It leverages certificates issued by trusted Certificate Authorities
(CAs), allowing for scalable and secure identity verification across large
ecosystems.
In this model, each client generates a private key and a Certificate Signing Request (CSR), which is then verified and signed by a trusted CA. The server is pre-configured with the CA's root certificate, enabling it to verify incoming client certificates during the TLS handshake. The server not only validates the certificate chain but also ensures the client holds the corresponding private key. Finally, the certificate is bound to a client identifier, enabling consistent identity mapping.
This method is ideal for federated or regulated ecosystems where trust is established through public or private PKIs—such as Open Banking networks, OpenID Connect ecosystems, and large-scale B2B API platforms with rotating or ephemeral certificates.
→ Want to learn more about mTLS client authentication flow? Click here to see OAuth Mutual TLS (mTLS) Client Authentication Explainedself_signed_tls_client_auth: Trust Without a CA
In contrast, self_signed_tls_client_auth provides a lighter-weight
authentication mechanism better suited to controlled or internal environments.
Instead of relying on a CA, clients generate self-signed X.509 certificates.
These certificates are not inherently trusted by the server and must be
explicitly registered or matched by subject Distinguished Name (DN).
Since there’s no external certificate authority involved, the server must be manually configured to recognize and trust each self-signed certificate. During the TLS handshake, the server validates the certificate based on its local trust store and binds the certificate to a client identity or access policy.
This approach is only recommended when both client and server infrastructure are under the same administrative control and where it’s feasible to manage trust relationships manually. It works well for testing environments, internal systems, or tightly controlled B2B integrations.
Quick Comparison: self_signed_tls vs tls_client_auth
| Feature | self_signed_tls_client_auth | tls_client_auth (CA-signed) |
|---|---|---|
| Certificate Issuer | Client (self-signed or internal CA) | Public or enterprise CA |
| Trust Model | Manual trust on server (certificate or DN match) | Validated against CA chain |
| Use Case | Closed/internal systems, POCs, dev environments | Production APIs, Open Banking, OAuth 2.0 mTLS |
| Authentication Strength | Strong (if trusted out-of-band) but prone to config drift | Strong with scalable trust via CA |
| Setup Complexity | Manual per-client trust configuration | CA infrastructure required but scalable |
| OAuth 2.0/OIDC Support | Supported (e.g., in private ecosystems) | Recommended in OAuth 2.0 mTLS specs |
When to Use Each Method
Choosing between tls_client_auth and self_signed_tls_client_auth depends on the
level of trust you require, who controls the infrastructure, and whether you
need to scale the solution across multiple clients or environments. Below are
some common scenarios that help illustrate which method is more appropriate
based on operational context and trust boundaries.
| Scenario | Recommended Method |
|---|---|
| API Gateway for internal microservices | self_signed_tls_client_auth |
| OAuth 2.0 confidential clients in production | tls_client_auth |
| CI/CD system calling internal deployment APIs | self_signed_tls_client_auth |
| Third-party fintech apps calling a banking API | tls_client_auth |
| Testing mutual TLS locally | self_signed_tls_client_auth |
In environments where both client and server are fully under your control—such
as internal microservices or CI/CD tooling—it’s often simpler and more efficient
to use self_signed_tls_client_auth. The overhead of managing CA-signed
certificates is unnecessary when you can directly configure the server to trust
known certificates.
However, for production-facing use cases involving external parties or requiring
regulatory compliance—such as financial APIs or OpenID Connect client
authentication–tls_client_auth is the preferred and more secure option. It
enables scalable trust using widely accepted PKI mechanisms, ensuring clients
are properly verified and their certificates managed in line with lifecycle and
revocation standards.
Always consider the operational burden, trust requirements, and audience for your APIs when deciding between these two approaches.
Security Considerations
Mutual TLS (mTLS) provides a robust method of client authentication, but the security of the overall system depends heavily on how certificates are issued, validated, and managed.
In both cases, the strength of the security model depends on operational discipline. Self-signed certificates can be secure if managed properly, but introduce a greater burden of manual trust management. CA-signed certificates shift that burden to a scalable, standards-based PKI model—reducing human error and supporting wider interoperability.
→ Decided on mTLS? Consider Binding Tokens to Certificates. Learn moreSelf-Signed Certificates
Using self_signed_tls_client_auth can still achieve strong authentication, but
only if the server is tightly configured. The server must explicitly trust each
certificate—usually by maintaining a local list of certificate fingerprints,
public keys, or subject DNs. This makes certificate management a manual process,
and any oversight (such as failing to revoke access when a client certificate is
compromised or rotated) can lead to security vulnerabilities.
To use self-signed certificates securely:
-
Trust must be configured out-of-band, ideally through a secure deployment process.
-
The certificate trust list should be kept small, current, and auditable.
-
Access control policies should tightly scope what each client is allowed to access, reducing the blast radius in case of compromise.
While suitable for internal environments, this approach does not scale well across teams or organizations and is vulnerable to misconfiguration.
CA-Signed Certificates
In contrast, tls_client_auth based on CA-signed certificates introduces a
scalable trust model rooted in Public Key Infrastructure (PKI). When a trusted
Certificate Authority issues a client certificate, the server can verify both
the certificate’s integrity and the CA’s identity automatically during the TLS
handshake. This approach supports:
-
Automated certificate issuance and renewal, often via protocols like ACME.
-
Centralized revocation using CRLs or OCSP.
-
Built-in auditability and compliance alignment, especially in regulated industries.
-
Trust chaining, which allows ecosystems to delegate trust across intermediate CAs.
This makes tls_client_auth well-suited for multi-tenant platforms, third-party
integrations, and environments where you need to securely onboard and manage
many clients without direct server-side trust configuration.
Conclusion
Choosing between self_signed_tls_client_auth and tls_client_auth isn't just a
matter of preference—it's a decision rooted in your system’s trust boundaries,
operational scale, and security posture.
If you're operating in a tightly controlled environment—such as internal services, development pipelines, or staging setups—self-signed certificates can offer simplicity and control. Just be sure to handle trust configuration and access control with discipline, as the manual nature of this approach leaves room for drift and human error.
For production systems–especially those exposed to third parties or governed by
regulatory standards–tls_client_auth is the clear choice. It enables automated
trust validation, aligns with existing PKI practices, and supports secure
onboarding at scale. Whether you're building Open Banking APIs, OAuth 2.0 flows,
or distributed B2B platforms, CA-signed certificates provide the rigor and
flexibility modern ecosystems demand.
Ultimately, both methods can be secure when implemented correctly. The key is to align your authentication strategy with your operational realities and risk tolerance—choosing the right tool for the right context.
As more than 80% of organizations expose sensitive data through poorly secured APIs, getting your client authentication right is only the beginning. Download our API Security Risk Report below to discover the most common mistakes enterprises make—and how to fix them before attackers find them first.
API Security Report
Helping Enterprises Recognize and Address Critical Risks
More than 80% of organizations are exposing sensitive data with weak API security
Download Now →